Programs that do not run in a sandbox can bypass the macOS system protection TCC as soon as the terminal is granted full disk access.
As developer and blogger Jeff Johnson discovered, programs can use a trick to circumvent macOS security measures and access all folders on the system if the terminal has full disk access rights.
According to Johnson, the gap only affects apps that are not running in the sandbox. This is mandatory for the distribution of programs via Apple’s App Store, but not for programs that find their way to the Mac via download or email, for example. Malicious software can start shell scripts included in the program bundle in the terminal with just a few lines of code. If the utility has full disk access, the script that is started also gets these rights and can cause damage or access data that an app otherwise has no access to.
Sandboxed apps are generally not allowed to start scripts in the terminal. macOS reports an error here. Programs obtained via the App Store cannot use the loophole.
How macOS Access Control protects data
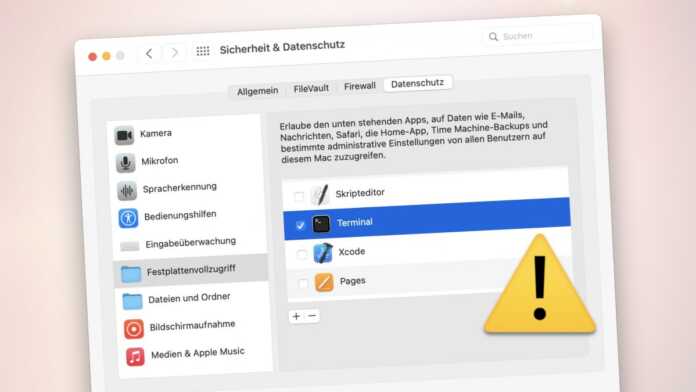
Normally, even Mac apps whose file system access is not restricted by a sandbox are not allowed to access folders such as Downloads, Documents or the desktop without asking. This access protection has been in effect since macOS 10.15 Catalina and higher and is provided by the “Transparency, Consent, and Control” (TCC) framework (see Apple for details). The “Security & Data Protection” system setting in the “Data Protection” tab in the “Files and Folders” area reveals what an app is specifically allowed to access.
In addition to the targeted access rights, there is full hard disk access, which is important for backup programs, for example, but is also often granted to the terminal by admins. Only with this authorization can a program also access generally protected folders such as “~/Library/Application Support/com.apple.TCC”. It contains, for example, the SQLite database from Apple’s TCC framework and is therefore normally protected against manipulation.
How to secure?
If you need full hard disk access in the terminal, you should only switch it on when necessary. Rarely are there cases in which it is permanently required. Without authorization, supposed malware that wants to exploit the gap described will also come to nothing.
Since the terminal has only limited rights by default, no action is required for users if they have never used it. However, a quick look at the “Security & Privacy” system settings in the “Full Hard Drive Access” section of the “Privacy” tab doesn’t hurt. The terminal should not be listed there or the checkbox should be deactivated.
If you only use apps from the App Store, you can switch the “Allow app download from” setting to “App Store” in the “General” tab in the “Security & Privacy” system settings. macOS then prevents programs from starting from other sources, such as malware distributed by e-mail.