In recent years Google has gradually strengthened the safety measures of Android, but with Android 16 the company takes a further step forward to protect users from one of the most insidious and difficult to identify threats concerning the network: the False cellular towers, known as Stingray.
These are devices that imitate a legitimate repeater of the mobile network and induce the phone to connect to a fictitious and unsafe network, allowing attacker or surveillance bodies to collect sensitive data or to intercept communications.
As often happens, these defense features require hardware innovations to be fully operational, and it is likely that they will initially arrive only on next generation devices such as the Pixel 10 series; Let’s see in detail what this novelty includes and which scenarios of use can cover.
Android 16 will send notifications if the smartphone connects to an unsafe network
To understand the importance of the new protection introduced by Android 16 it is useful to retrace the functioning of the Stolingy, these devices are positioned near the target and behave as fake repeateners of the cellular network:
- The phone connects automatically convinced of communicating with an authentic infrastructure
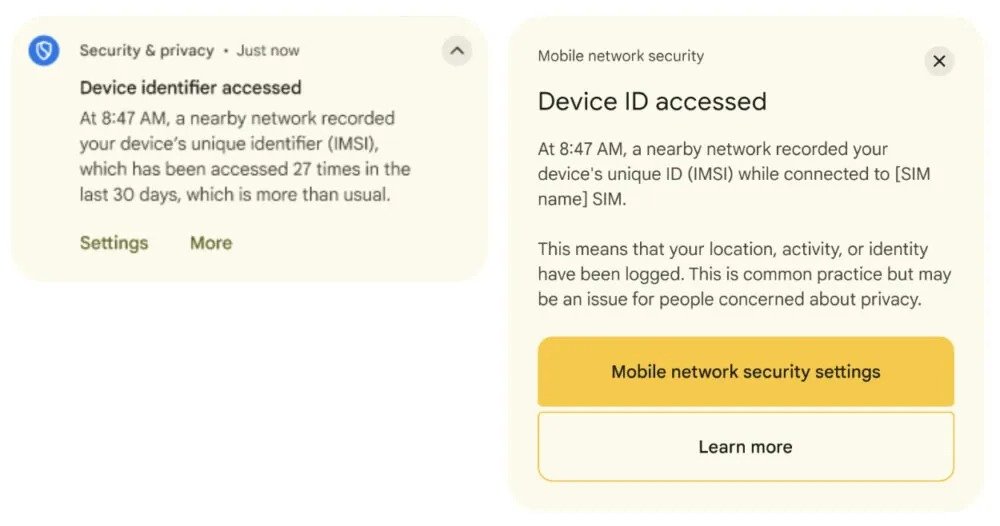
- The attacker can collect unique identification of the device, such as IMEI and IMSI
- In some cases it can force the downgrade of the connection by obliging the use of old and less safe protocols (for example 2G networks or null numbers)
- messages and calls are no longer encrypted by becoming easily intercepted
Just the ability to force weak protocols and to collect data without the user noticing it makes these tools extremely dangerous, to the point that they are used not only by law enforcement agencies, but also by hostile or criminal actors.
It is not the first time that Google moves in this direction, Android 12 had introduced the possibility of deactivating the 2G network on a modem level to reduce the risks of downgrade, Android 14 has made it possible to block connections that use null figures (i.e. communications without encryption), while Android 15 added the possibility for the operating system to receive notifications when the network requires unique identifiers or attempts to change Figure algorithm.
The main problem? These features depend on an update of the modem drivers, therefore many devices (including current pixels) cannot yet take advantage of it.
With Android 16 Google decided to try again, reintroducing and expanding the settings page dedicated to Safety of the mobile networkaccessible following the path Settings -> Security and Privacy -> Safety of the Mobile Network.
This page contains two main options (both deactivated by default):
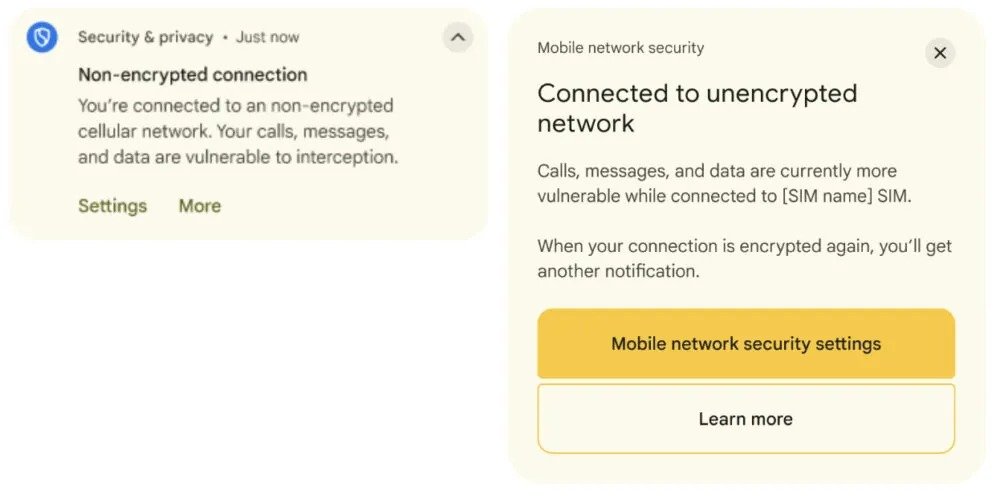
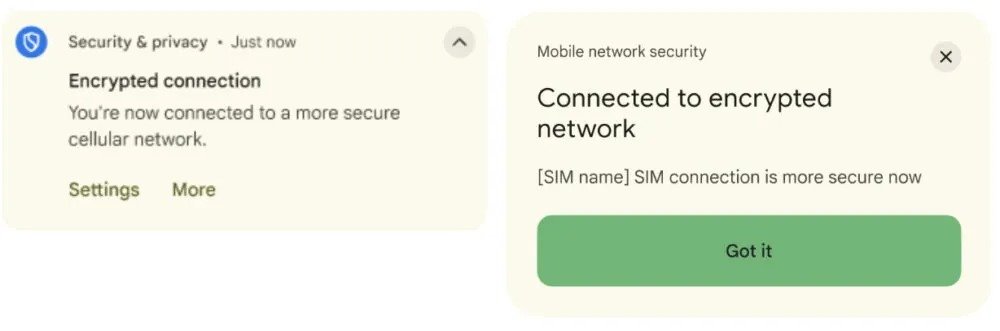
- Network notifications -> If you activate the system, it warns when the device connects to a non -encrypted network or when the network requires unique identifiers, the notifications appear both in the notifications panel and in the safety center
- Network protection 2G -> allows you to completely disable 2G connectivity
In practice If the smartphone connects to a non -encrypted network, the user will display a clear message with the date and time of the eventso that you can evaluate whether to disconnect or act accordingly.
Unfortunately, the new settings page will only be available on devices that meet two requirements, i.e. the support for deactivation of the 2G network and the support for network notifications (they require version 3.0 of Iradio Hal, the hardware abstraction layer that manages the communication of the modem).
This means that No current pixels, even if updated to Android 16, will benefit from these notifications; It will therefore be necessary to wait for the next devices launched with Android 16 pre -installed, such as the Pixel 10 series.
Despite this limit, Google’s move remains important, sets a new minimum safety standard for the management of mobile networks and could encourage manufacturers to integrate the new compatible modem.
Stolingy will not disappear from today and will continue to represent a difficult threat to identify, however the integration of notifications that report in real time suspicious connections and security downgrades is a decisive step forward.
Users will still have to remain vigilant and adopt good practices, but the possibility of receiving an automatic warning in case of malicious nets is a protection measure that until recently seemed unrealizable on a large scale. We just have to wait for the arrival of the first compatible devices to touch these new features.

